Quantum Cryptography: Securing the Future of Communication
- sciforum

- Sep 25, 2025
- 11 min read
TABLE OF CONTENTS
1. Introduction
2. Transition from Classical to Quantum Cryptography
3. Pioneers of Quantum Cryptography
4. Quantum Cryptography
5. Quantum Key Distribution (QKD)
6. Quantum Key Distribution Models
7. How Quantum Cryptography is Changing Data Security
8. Limitations of Quantum Cryptography
9. Challenges Ahead
10. The future of Data Security
11. Conclusion
12. References
Abstract
The emergence of quantum cryptography has shifted the landscape of digital security. While classical encryption methods utilize advanced mathematics, quantum cryptography uses the very laws of physics to secure data in all forms. This blog will explore the evolution of classical cryptography into the realm of quantum-based methods, with a focus on early work surrounding two of the first protocols for quantum key distribution: BB84 and E91. It will define how quantum key distribution works, why it has been implied to negate the threat of quantum computing, and some of the barriers still ahead. By the end of this blog you will have a better understanding of how quantum cryptography could change the landscape of cybersecurity and facilitate secure communication in a world powered by quantum computing.
Introduction
In the digital age, security is the backbone of everything we do such as online banking, private messaging, cloud storage, and even national defense. Most of this security relies on mathematical algorithms, such as RSA (Rivest, Shamir, and Adleman) and AES (Advanced Encryption Standard), which are considered secure because they take an impractically long time for today’s computers to break. But what happens when computers become powerful enough to crack them in minutes?
That’s not just a theoretical question anymore. With the rapid development of quantum computers, the once-safe assumptions of modern cryptography are under threat. Quantum computers can process information in fundamentally different ways, using principles like superposition and entanglement to solve problems far faster than classical computers. This looming security crisis forces us to ask, Can we rely on traditional math-based encryption in a post-quantum world?
Surprisingly, the answer might come from the very science that is challenging our current security- quantum physics itself.
Welcome to the world of quantum cryptography. So what’s quantum cryptography?
It's a revolutionary approach that uses the laws of physics, rather than mathematical complexity, to protect information. At its core, quantum cryptography harnesses the strange behaviors of particles at the quantum level to create unbreakable encryption keys. Unlike traditional encryption, which can be broken if enough computational power is available, quantum cryptography offers a level of security rooted in the fundamental rules of nature.
In this blog series, we’ll explore how quantum cryptography works, why it’s considered a game-changer in cybersecurity, and what it means for the future of data protection. As we stand on the edge of a quantum-powered era, it’s time to rethink what “secure” really means and how physics might hold the key.
Transition from classical to quantum cryptography
In the early days, classical cryptography was the primary method used to secure information. It involves using mathematical algorithms to transform data into a coded form, known as encryption, so that only those with the correct key can read or access the original message.
And for decades, classical cryptography was like the superhero of digital security, the unstoppable guardian keeping secrets safe from the evil clutches of hackers everywhere. It was everywhere you looked, locking down your online bank account, guarding government secrets, and even hiding your embarrassing search history from nosy neighbors. Algorithms like RSA and AES became the shining stars, trusted by millions to keep data locked tighter than a vault in Fort Knox. You could say classical cryptography was the king of security, powerful, reliable, and absolutely essential in the digital world. Without it, the internet would have been like a wild west saloon, where anyone could sneak a peek at your private messages.
However, with the advent of quantum computing, confidence in classical cryptographic methods began to waver. Quantum computers possess the ability to solve certain mathematical problems exponentially faster than traditional computers, directly challenging the security assumptions underlying algorithms like RSA and AES. This development raised significant concerns within the cybersecurity community, as it implied that encryption schemes once considered secure could potentially be broken with relative ease in the near future. As a result, researchers and organizations started exploring new approaches to ensure data protection in a world where classical methods might no longer suffice. Instead of just using hard math problems, they began to use the strange rules of quantum physics to protect data. This led to the creation of quantum cryptography, which uses how tiny particles behave to create security that even the most powerful computers can’t break. This was a big change in how we think about keeping information safe and opened up new possibilities for truly secure communication.
Pioneers of quantum cryptography
Quantum cryptography's journey began with early attempts to secure information, such as the scytale cipher used by the ancient Greeks around 400 BC or the Alberti cipher wheel developed during the Renaissance. Eventually, these methods evolved into complex modern encryption techniques that involve quantum computation. Artur Ekert, a cryptophysicist at the University of Oxford) A pioneer in the field explains how early cryptographic techniques paved the way for modern encryption. Artur Ekert's work played a pivotal role in merging cryptography and quantum physics. He demonstrated how Bell’s inequalities, which talk about the fundamental aspect of quantum mechanics, could secure communication through the inherent randomness of quantum systems.
In the early 1970s, Stephen Wiesner introduced quantum conjugate coding. His initial ideas, though ahead of their time, laid the groundwork for using quantum properties to encode information. He proposed a method to store two messages in a single photon using "conjugate observables," such as the linear and circular polarization of photons, so that only one message could be decoded at a time.
The true breakthrough came in 1979 when Charles H. Bennett and Gilles Brassard combined Wiesner's concepts with a new understanding: photons were not meant to store information, but to transmit it securely. They realized that any attempt to intercept the photons would inevitably alter their quantum state, a change that would be detectable by the sender and receiver. This led to the creation of the BB84 protocol, the first quantum key distribution (QKD) system.
In 1991, Artur Ekert introduced an entirely new method with his E91 protocol. Diverging from BB84's single-photon approach, Ekert's protocol is based on quantum entanglement. He demonstrated that a secure cryptographic key could be created using entangled photon pairs, where the security is verified by testing for the violation of Bell's inequalities. This work proved that entanglement-based systems were an equally robust and valid alternative for quantum key distribution.
Quantum Cryptography
It is a field of cybersecurity that applies the principles of quantum mechanics to protect data. Unlike traditional encryption, which is based on complex mathematical problems, quantum cryptography's security is guaranteed by the laws of physics. The core idea is that any attempt to observe or copy a quantum system, like a photon will inevitably alter its state, thereby alerting the user to the presence of an eavesdropper.
It uses photons to transmit cryptographic keys over fibre optic wires, using the basic principles of quantum mechanics for encryption such as:
●The particles that make up the universe are not only inherently uncertain but also exist in more than one state simultaneously.
● A quantum property cannot be observed without changing or disturbing it.
● The no-cloning theorem states that it is impossible to create an identical copy of an entire quantum particle.
● Photons are randomly generated in one of two quantum states.
All these principles mark the basis of cryptography.
Quantum Key Distribution
It is the most mature and practical application of quantum cryptography. QKD is not a method for encrypting entire messages, but rather a highly secure way to generate and distribute a secret cryptographic key between two parties. This key can then be used with conventional, fast encryption to secure communication.
It uses a series of photons to transmit data from one location to another over a fiber optic cable. It’s a method that uses the above principles to generate and distribute cryptographic keys. By comparing the properties of these photons, the two endpoints can determine the keys, ensuring that any eavesdropping attempt is detectable. Quantum Cryptography follows a model developed in 1984 in which the photons represent binary bits: 0s and 1s. The data is converted into bits of 0s and 1s which are transmitted using polarised photons. These are then put into a particular quantum state by the sender and are observed by the recipient. The sender transmits photons through a filter (or polarizer) which randomly gives them one of four possible polarizations and bit designations: Vertical (One bit), Horizontal (Zero bit), +45 degrees right (One bit), or -45 degrees left (Zero bit) . The receiver can distinguish the data between 90 and 0 degrees or -45 and +45 degrees polarization. The photons travel to a receiver, which uses beam splitters to read the alignment of the particular photons. The receiver not only needs to receive the signals but also has to measure them with the exact alignment as the receiver does not know which beam splitter to use for each photon and has to guess which one to use. Once the entire set of photons has been sent, the receiver tells the sender which splitter was used for each photon in the exact sequence. The sender then compares this information with the splitters and sequence of polarizers they used to send the key. The photons that were read using the wrong beam splitter are discarded and thus the resulting sequence of bits becomes the key. Now, if a photon is intercepted by an eavesdropper, its state will change, as one can't measure a quantum property without disturbing it. The change will be detected by both ends, making it impossible to read any information or photons without being detected. A simple demonstration shown below explains the working process. In the field of cryptography, Alice, Bob, and Eve are fictional characters often used to represent two parties communicating over a network.
![A diagram explaining the quantum key distribution [SOURCE:quantumxc.com]](https://static.wixstatic.com/media/b274d4_e99aa38f2c064fab86cffe5d90fa1a63~mv2.png/v1/fill/w_650,h_472,al_c,q_85,enc_avif,quality_auto/b274d4_e99aa38f2c064fab86cffe5d90fa1a63~mv2.png)
Assume you have Alice and Bob who wish to transmit a secret from one to another that cannot be intercepted by a third party. Using QKD, Alice gives Bob a chain of polarized photons through an optical fiber. The cable need not be kept secure since the photons possess an arbitrary quantum state. If an eavesdropper, Eve, attempts to intercept the conversation, she must read every photon to read the secret. Next, she needs to forward that photon to Bob. When she reads the photon, Eve changes the quantum state of the photon, and this puts errors in the quantum key. This is what signals Alice and Bob that someone is intercepting and the key has been tampered with, so they abandon the key. Alice must send Bob a fresh key that is not compromised, and then Bob may use that key to decrypt the secret.
Quantum Key Models
There are two widely recognised QKD models that play a significant role in this field:
Prepare-and-Measure Protocols: These protocols, exemplified by the famous BB84 protocol (developed by Bennett and Brassard in 1984), rely on one party preparing and sending quantum states to the other. The security is based on the measurement-disturbance principle.
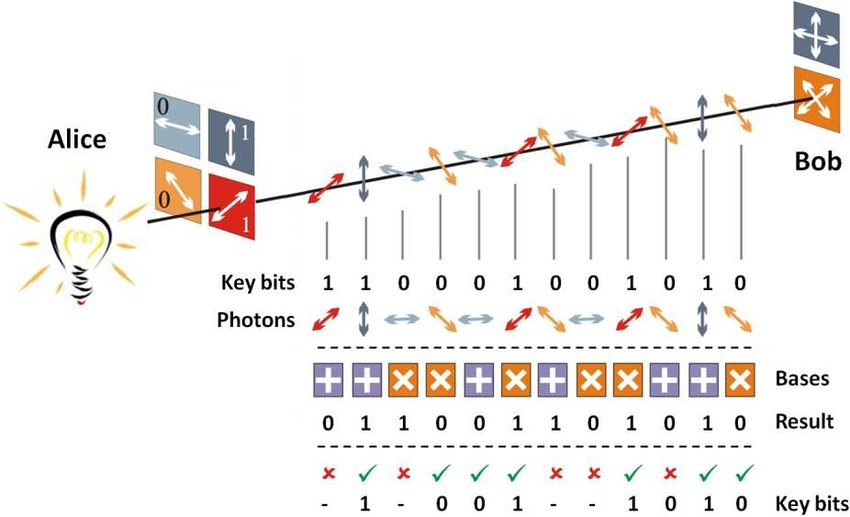
BB84 Protocol: Introduced by Bennett and Brassard in 1984, this is considered the first practical QKD method which uses the polarization of photons to encode information. It follows the same method as discussed earlier, which makes it impossible for the eavesdropper to intercept any data without being detected.
Entanglement-Based Protocols: This family of protocols, first proposed by Artur Ekert in his E91 protocol, uses quantum entanglement as its resource. Here, a source distributes pairs of entangled photons to both parties. Because the properties of these entangled particles are correlated, measuring one instantly affects the other.
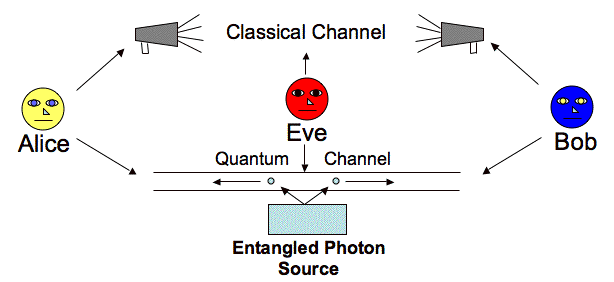
Proposed by Artur Erkut in 1991, it works on the principle of quantum entanglement, which states that aspects of one particle of an entangled pair depend on aspects of the other particle, no matter how far apart they are or what lies between them. In this there is a single source that emits a pair of entangled photons with Alice and Bob receiving each particle. Similar to the BB84, Alice and Bob would exchange encoded bits and match splitters. Howeve,r this time due to the principle of entanglement, the outcome of their matching case will always be opposite. Either of them will have complement bits in bit strings interpreted. One of them can then invert bits to agree upon a key.
Thus practically it is not possible to have a third photon in entanglement with energy levels sufficient for non-detectability, making this system fully secure.
How Quantum Cryptography is changing Data Security?
The Shift from Classical to Quantum Security
Modern encryption systems like RSA (Rivest–Shamir–Adleman) and ECC (Elliptic Curve Cryptography) have long been the backbone of secure communication. These systems rely on mathematical problems that are extremely difficult for classical computers to solve.

● RSA Encryption: Security is based on prime factorization. Two large prime numbers are multiplied to form a product. While encrypting is easy, decrypting requires factorizing this large number back into its prime components—a task that could take classical computers thousands of years.
● ECC Encryption: Security is based on the Elliptic Curve Discrete Logarithm Problem (ECDLP). A private key (a random number) is multiplied with a base point on an elliptic curve to generate a public key. Reversing this process to find the private key is practically impossible for classical computers.
However, quantum computers change the game. Using Shor’s algorithm, they can efficiently factorize large numbers and solve ECDLP, breaking both RSA and ECC encryption. This makes traditional cryptography vulnerable in a quantum-powered future.
Why is Quantum Cryptography Needed?
Since quantum computers can easily bypass classical encryption, a new approach is required, one that doesn’t rely on mathematical complexity but on the laws of physics. Quantum cryptography, particularly Quantum Key Distribution (QKD), ensures that data remains secure even in the presence of quantum computing.
Impact of Quantum Cryptography on Data Security
1. Secure Communication: Unlike traditional cryptography, quantum cryptography leverages physical principles, making it resistant to brute-force attacks.
2. Future-Proof Protection: Data encrypted today remains secure even when quantum computers become mainstream.
3. Eavesdropping Detection: Any attempt to intercept quantum-encrypted data alters its quantum state, immediately alerting users to intrusion.
4. Increased Trust and Reliability: Organizations adopting quantum cryptography can ensure stronger data protection, boosting confidence among partners and clients.
Limitations of Quantum Cryptography
1. Error Sensitivity: Photon polarization changes can introduce transmission errors.
2. Range Constraints: Reliable transmission is limited to about 400–500 km without specialized equipment.
3. High Infrastructure Cost: Dedicated fibers, repeaters, and specialized hardware make it more expensive than classical systems.
Challenges Ahead
● Scalable Photon Sources: Developing reliable single-photon generators for long-distance communication.
● Efficient State Transfer: Improving methods to transmit quantum states faster and more reliably.
● Protocol Standardization: Establishing unified models for practical and widespread adoption.
● Public Acceptance: Building trust among governments, industries, and consumers.
● Shared Network Design: Creating cost-effective topologies that allow multiple users to connect securely.
The Future of Data Security
Quantum cryptography represents a paradigm shift in cybersecurity. While challenges remain in scalability, cost, and adoption, its potential to secure communication against even the most powerful quantum computers makes it a cornerstone of future-proof data protection. Organizations that begin exploring and investing in quantum-safe solutions today will be better prepared for the quantum era of tomorrow.
Conclusion
As we move into the quantum era, the very foundations of digital security are being challenged. Classical cryptographic systems that once felt unbreakable are now vulnerable to the immense power of quantum computing. Quantum cryptography steps in as a revolutionary solution, offering protection not through mathematical complexity, but through the unchanging laws of physics. With techniques like Quantum Key Distribution (QKD), secure communication becomes not just stronger, but fundamentally different—where any intrusion can be instantly detected.
While limitations in cost, scalability, and infrastructure remain, the progress in this field signals a future where quantum-safe communication could become the global standard. The shift from classical to quantum cryptography is more than just a technological upgrade; it is a paradigm change in how we define and ensure security in the digital age. Embracing this change today will prepare us for a safer, more resilient tomorrow.
References
BBVA
The pioneers of quantum cryptography, recognized with the Frontiers of Knowledge Awards
National Institute of Standards and Technology (NIST)
What Is Quantum Cryptography
https://www.nist.gov/cybersecurity/what-quantum-cryptography
BlueQubit
Quantum Cryptography: Applications, Benefits, and Limitations
IBM
What Is Quantum Cryptography?
By: Harsh Raj, Simpy Prerna, Samridhi and Sreesathya Bhardwaj

Comments